Apparently we’ve been targeted again due to unknown WordPress theme source code being uploaded to one of our hosting account by our client. The code files left a backdoor for hackers to inject malicious code again.
Please please please remember don’t upload “FREE THEME” or “Plugins” from unknown source, most of the time they have backdoor with it. A lot of WordPress users (not programmers) apparently don’t know the underlying danger behind all these code files. p.s: i’ve been one of them before.
Unluckily our website became one of the victims,
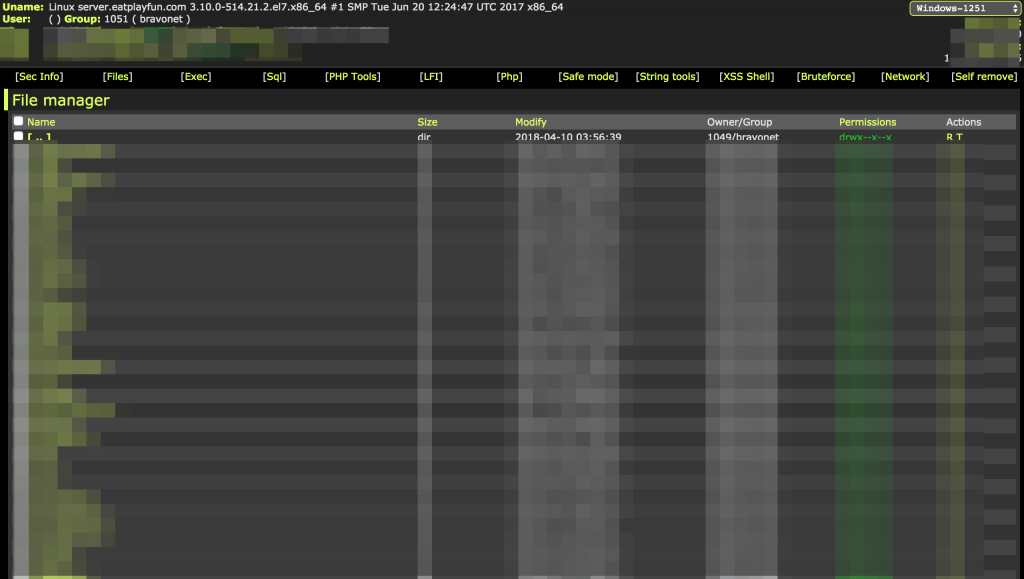
Lucky, we found out early. They manage to upload web shell “WSO 2.6” and apparently this script manage to bypass shell,exec etc PHP default functions.
Several harms that they had done on the side including mass content edit & mass password change etc.
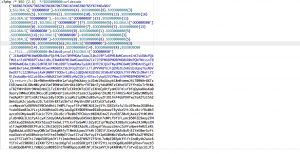
The web shell script injected has been encrypted
So what’s our approach?
It seem impossible to prevent all these suspicious code to run by hardening PHP with disable_functions. The malicious code needs safe_mode to be off which is not possible to widely enable in PHP5.6 (safe_mode has been removed since PHP5.4).
I realised that they started the attack at midnight 2.30 AM, probably run by bot to scan and look for all the files that’s possible planted by them in some of the directories.
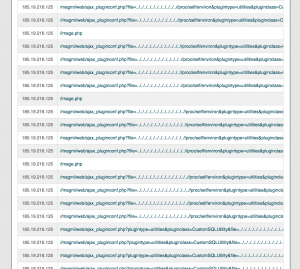
We did some security prevention in our server to prevent all these code being injected again and reduce the possibility of being execute.
Educating our clients is the most important part in the entire experience.
If you are facing any security problem, feel free to look for advise from us.
